Tenant Restrictions Made Easy with Global Secure Access
In certain scenarios, organizations may want to restrict access to other tenants to prevent potential data leakage or for other security reasons. Often, there is also a need to block access to Microsoft personal accounts, such as Outlook.com or personal OneDrive. Historically, implementing such restrictions on Windows workstations was somewhat challenging. Now that Global Secure Access is generally available, this process has become significantly more straightforward by leveraging Microsoft Traffic Profiles.
Microsoft traffic profile is included with the Secure Access Essentials license, which will soon be included in the Microsoft 365 E3 license.
Let's consider a scenario where an employee attempts to sign in to their personal Microsoft account from a corporate device. With Tenant restrictions V2 and client-side tagging with Global Secure Access, this access attempt will be blocked, ensuring that corporate data is not inadvertently shared with personal accounts.
So, what are the necessary steps to implement this?
First, we need to configure Tenant Restriction in the Microsoft Entra admin center by navigating to External Identities > Cross-tenant access settings. In the Default settings tab, you will find the Tenant Restrictions option. Set access status to block access.
Next, we need to navigate to Global Secure Access and activate Microsoft traffic profile.
If you want to test all the features of Global Secure Access, including Microsoft Entra Internet Access and Private Access, there is a 90-day trial available for the Microsoft Entra Suite license.
After enabling the profile, we need to assign it to a group of users.
NOTE: Access is granted only to users directly in the group and does not extend to nested groups.
We also need to activate Tenant Restriction within the Session Management section under Settings.
The final step is to deploy the client to your Windows devices, which is a requirement to tunnel network traffic to the Global Secure Access service. You can download the client from the Client Download section or directly via this link.
If you plan to deploy the client using Microsoft Intune or other device management tool, you can utilize the following commands:
GlobalSecureAccessClient.exe /install /quietGlobalSecureAccessClient.exe /uninstallOnce the client is installed on your device you should check the status and make sure that the Microsoft traffic profile was downloaded. In the system tray, right-click the Global Secure Access Client and select Advanced Diagnostics. In the Forwarding profile, you should see Microsoft 365 rules.
If everything was set up correctly, you should no longer be able to log in to Microsoft Personal OneDrive and Mail. The same restriction should apply if you attempt to use a separate account from an unknown tenant.
Test logging in with a separate account from an unknown tenant:
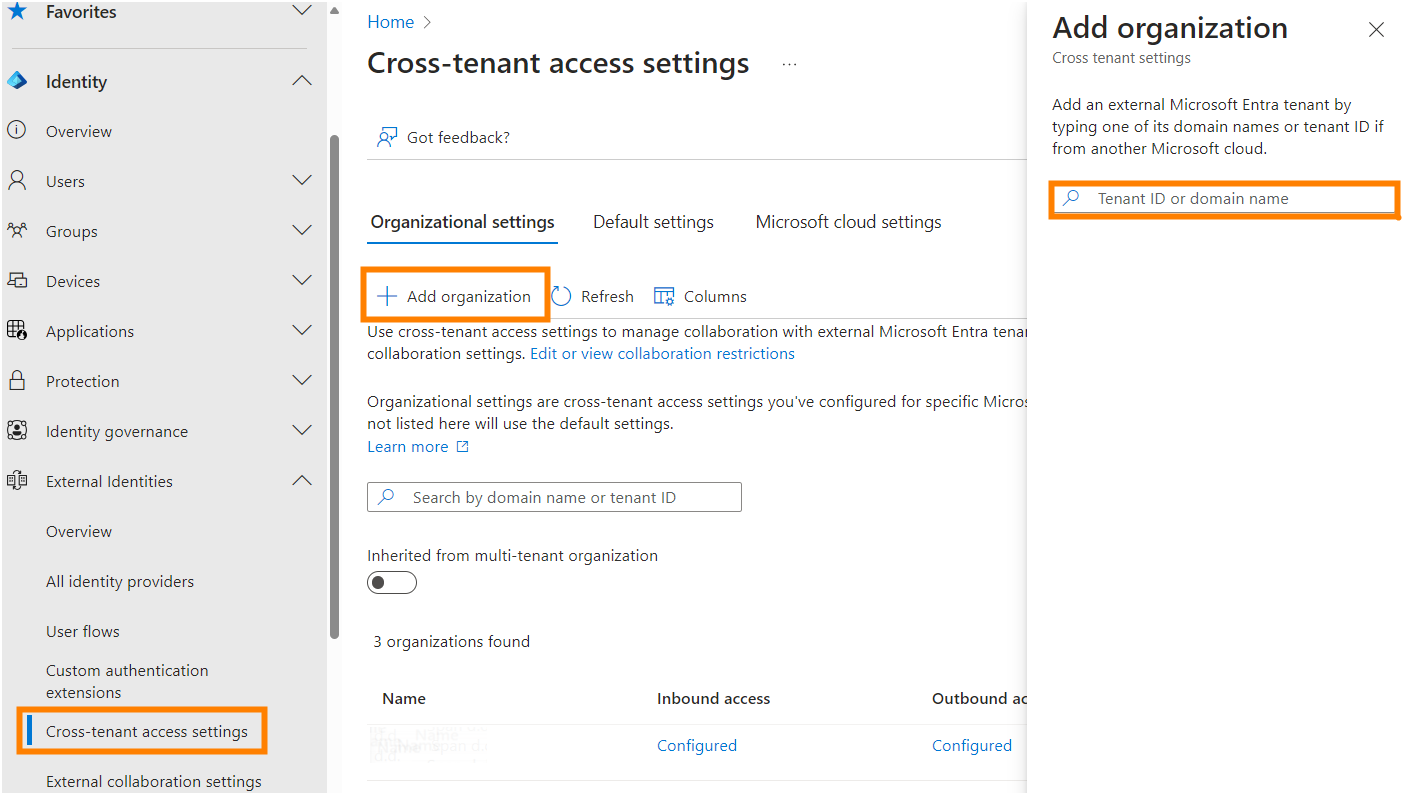
Of course, there are always exceptions. If you want to allow access to a specific tenant, you need to add the organization first by navigating to External Identities > Cross-tenant access settings and selecting Add organization.
Once the organization is added, you need to configure the tenant restrictions for that specific tenant to allow access.
If you haven't yet tried Global Secure Access, now is the perfect time to explore its capabilities. As Global Secure Access is a comprehensive product, I plan to dive deeper into its features and functionalities in future blog posts. Stay tuned for more insights and tips on maximizing the benefits of this essential security solution.