Stop Flying Blind: Get Visibility into Your Entra ID Enterprise Applications
The topic of Enterprise Applications in Entra ID is something that, not long ago, made me feel uncertain. The reason was simple. I honestly did not fully understand how to approach it from a security perspective.
It was clear to me that controlling app registration and consent was crucial. In most environments, I managed to enforce that new applications require admin approval before being added. Every time I achieved that, my next comment was always the same.
“Great, but do not forget to check the existing applications because there might already be something risky in there.”
And without fail, the next question I received was: "Okay, but how do we even do that? Do I have to open every single app manually?"
In such cases, I usually pointed people to various scripts or tools that could export data about enterprise apps, helping them make informed decisions about what is safe to keep.
But recently, I started wondering if I could create something like this myself using AI to speed up the process. Since I am not a coder, building a custom tool from scratch was never realistic, so turning to AI felt like the logical way forward.
First, Understand the Basics
Before I could even think about building a reliable report, I realized that I did not fully understand how Enterprise Applications, Service Principals, and App Registrations really work. If I could not explain them clearly to myself, there was no way I could ask AI to help me build a meaningful tool.
At this point, I have to give credit where it is due. Martin Heusser’s blog posts on the topic were a game-changer for me. I read both of his articles multiple times until I felt like I truly understood the concepts. If you are in the same boat, I highly recommend his content because it really helps connect the dots.
What I Wanted to Achieve
Armed with new knowledge, I went back to my script with a clear goal. I wanted a full report of all Enterprise Applications, not just App Registrations.
The reason is simple. I needed visibility over everything tied to my tenant, not only apps registered locally but also external ones, including third-party integrations that can access Exchange Online, OneDrive, and other sensitive Microsoft 365 services. To make the report more relevant, I also added exceptions to filter out certain built-in applications that are not important for my analysis and do not need to show up in the results.
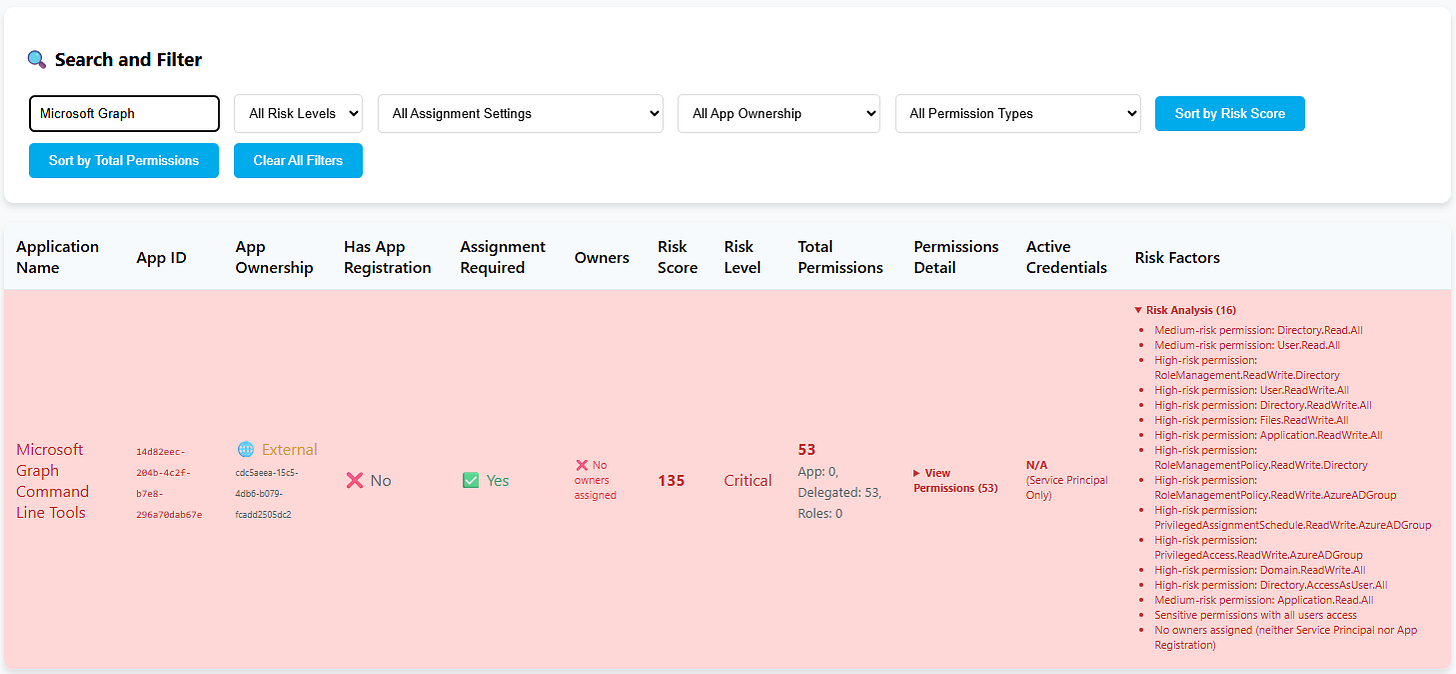
The HTML report includes:
App Ownership to quickly identify what kind of application it is.
Has App Registration to show if the app is registered in your tenant and holds active credentials.
Owners because you need to know who to contact about a specific app.
Assignment Required an often-overlooked parameter that defines whether users can access the app freely or only when explicitly assigned. For example, by default any signed-in user can query Microsoft Graph for basic directory information unless you restrict it.
Permissions Overview probably the most critical part, listing what rights the enterprise app or service principal holds.
Adding a Risk Factor
Without some kind of risk score, every app looks equally important, which makes cleanup nearly impossible. So I built a simple logic into the script that analyzes permissions and assigns a Risk Score and Risk Level to each app. These factors are customizable. You can tweak them to match your own risk appetite.
The Result
After a few weeks of trial and error, many iterations with AI, testing, and fixing mistakes, I finally ended up with a script that I felt was worth sharing. I have already used it to analyze several tenants, and let me tell you, the first report will probably hurt. But at least you will have a starting point for cleaning up potentially dangerous apps in your environment.
One thing is certain. Right now, most environments are flying blind when it comes to Enterprise Applications in Entra ID. And that needs to change.
Where to Get the Script
If you want to try this out in your own environment, the script is publicly available on my GitHub.
You can find it here: Get-EntraIDServicePrincipalReport.ps1
Use the script, change it if you want, adapt it to your needs, it is up to you. I will keep improving it and may even incorporate feedback from the community.
Prerequisites and Installation
Before running the script, ensure you have the required Microsoft Graph PowerShell modules installed:
Install only necessary modules
Install-Module -Name Microsoft.Graph.Authentication,Microsoft.Graph.Applications,Microsoft.Graph.Identity.SignIns,Microsoft.Graph.Identity.DirectoryManagement,Microsoft.Graph.Reports -Scope CurrentUser -AllowClobberOr install the full umbrella module
Install-Module -Name Microsoft.Graph -Scope CurrentUser -AllowClobberThe script automatically requests the minimal required permissions:
Application.Read.AllDirectory.Read.AllDelegatedPermissionGrant.Read.AllRoleManagement.Read.Directory
Available Parameters
The script offers several filtering options to optimize performance and focus analysis:
# Basic usage - analyze all Enterprise Applications
.\Get-EntraIDServicePrincipalReport.ps1
# Filter for apps with permissions only
.\Get-EntraIDServicePrincipalReport.ps1 -OnlyWithPermissions
# Minimum permission threshold
.\Get-EntraIDServicePrincipalReport.ps1 -MinimumPermissions 5
# Focus on internal applications with registrations
.\Get-EntraIDServicePrincipalReport.ps1 -OnlyWithAppRegistrations
# Analyze only service principals without registrations
.\Get-EntraIDServicePrincipalReport.ps1 -OnlyServicePrincipals
# Custom output location
.\Get-EntraIDServicePrincipalReport.ps1 -OutputPath "C:\Reports\MyReport.html"
# Use external risk configuration
.\Get-EntraIDServicePrincipalReport.ps1 -RiskConfigPath "risk-rules.json"The script includes intelligent pre-filtering that applies quick filters first, skipping detailed analysis for applications that don't meet criteria. This significantly improves performance when analyzing large tenants with hundreds of applications.
Report Output
The generated HTML report provides:
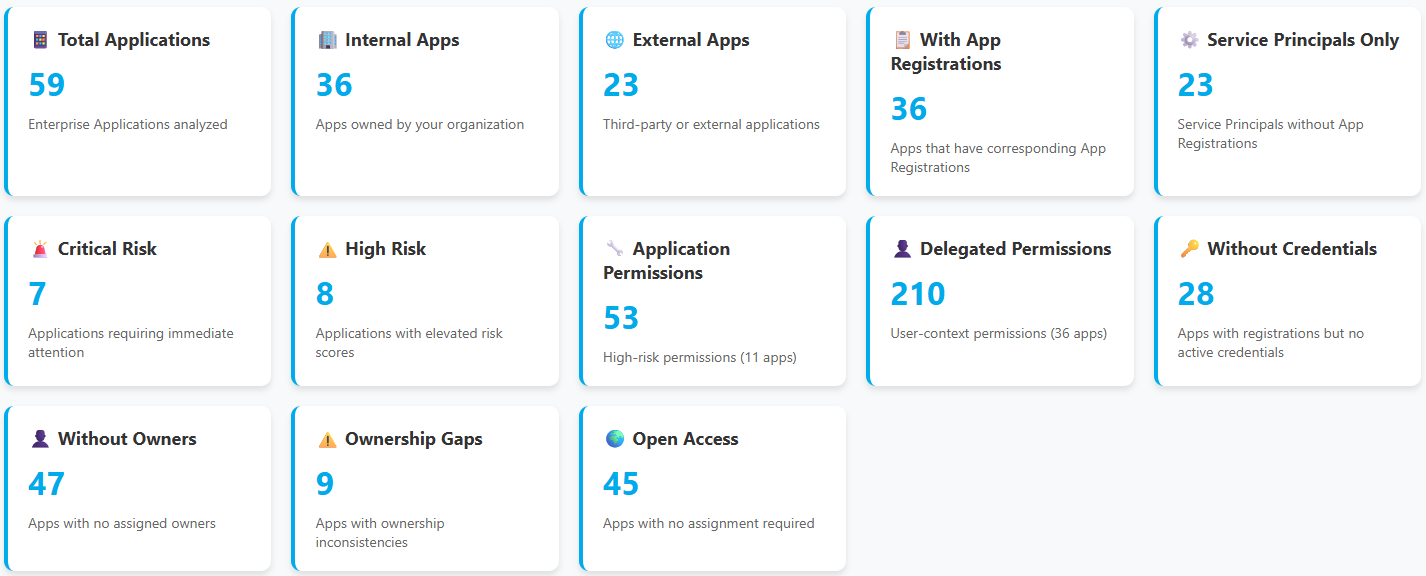
Executive-style dashboard with key metrics and risk statistics
Interactive filtering directly in the HTML report by risk level, ownership, assignment requirements, and permission types
Sortable columns for risk score, permission counts, and other attributes
Detailed permission breakdowns with expandable sections
Ownership analysis including gap detection for governance
Credential status tracking for active secrets and certificates
Risk factor explanations for each application's security posture
The report automatically opens in your default browser and includes comprehensive legends explaining all indicators and classifications.